We are excited to bring you MOBILedit Forensic 9.0, with powerful new features such as smartwatch forensics, cloud forensics, and even stronger security bypassing. With this new version, we are completing another important step in our mission to bring you additional evidence and help solve your cases.
Smartwatch forensics
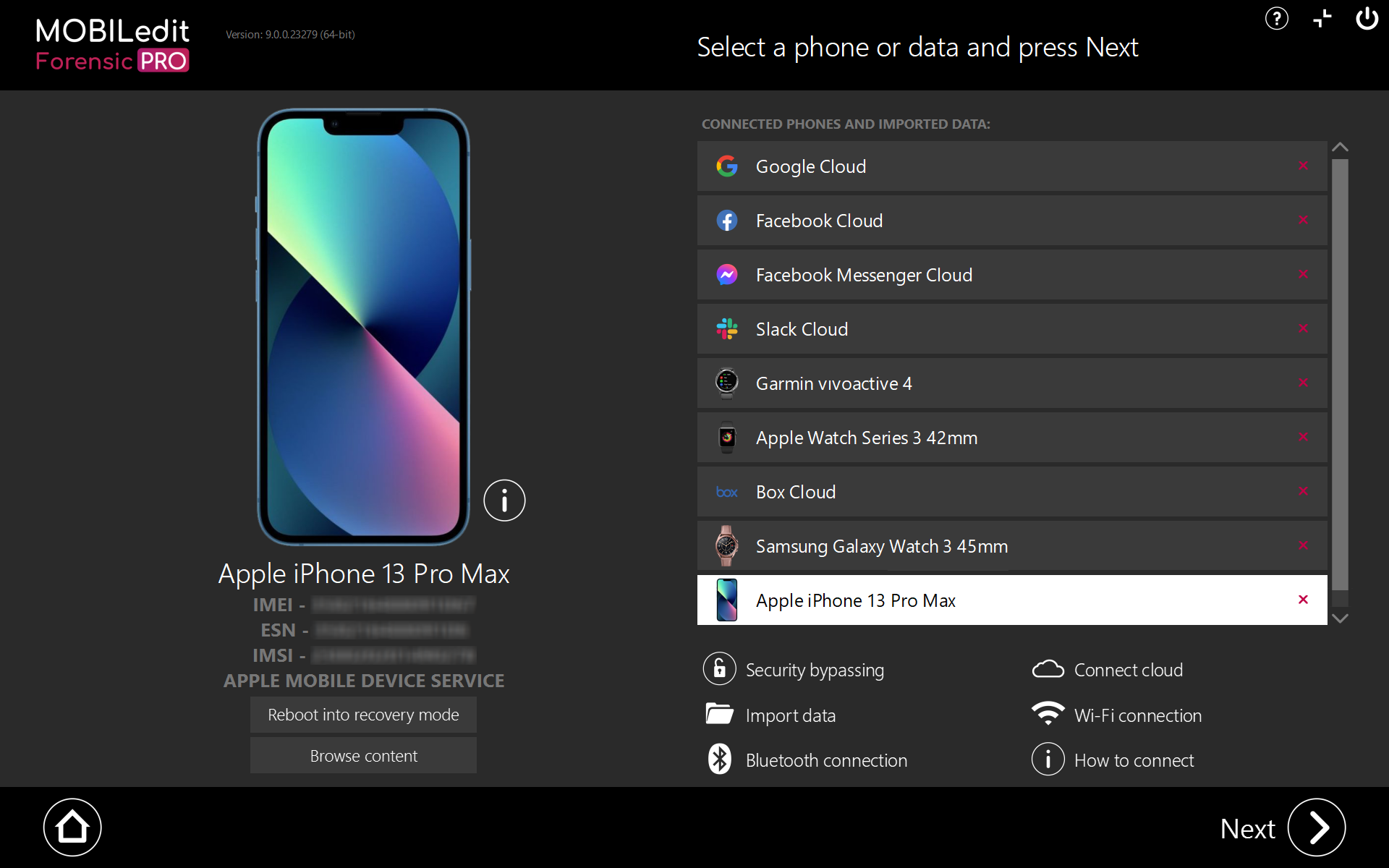
The personal data found in smartwatches can lead you in the right direction, especially when the phone is nowhere to be found. With the growing popularity of smartwatches, your investigations will be incomplete without retrievable smartwatch data. MOBILedit Forensic 9.0 can extract heartbeat details, which gives you an intimate look into the life of the user. This data reveals moments of excitement, stress, and even the time of death. For a successful investigation, examining smartwatches is a necessity. In addition to Apple Watch, MOBILedit now also supports the extraction and analysis of smartwatches from Garmin, Samsung, TCL and more.
Also introducing the Smartwatch Kit - a set of readers and cables that provides everything you need to connect to smartwatches.
Cloud forensics
In today’s world, data stored on a mobile device is only a snapshot of the overall data. That’s why we developed MOBILedit Cloud Forensic. Investigators can obtain the cloud log-in information from the phone itself and use it to look for evidence where they couldn’t before. We are now bringing this new function to you.
MOBILedit Cloud Forensic is available in 2 editions:
Add-on for MOBILedit Forensic PRO license, or
Standalone product MOBILedit Cloud Forensic
Currently supported clouds include: Box, Dropbox, Facebook, Facebook Messenger, Google Drive, Google Contacts, Google Calendar, Google Keep, Instagram, LinkedIn, Microsoft Onedrive, Twitter, Slack, FTP, IMAP, and POP3.
Stronger phone unlocking
Improved rooting support for Android, with new methods added to gain temporary root access, allowing for physical acquisition and access to more data for analysis. Also, Dirty COW works on more devices than before.
Decrypted physical images can be extracted from rooted devices that are using full disk encryption (FDE)
Physical images from more Spreadtrum devices can be extracted
EDL programmers can automatically be detected and matched with a connected Qualcomm device.
Choose multiple programmers to run at the same time like EDL, MTK DA, and others making for a quicker process and more efficient security bypassing.
Other improvements
Screen capturing - a new feature that semi-automatically scrolls and takes screenshots of entire conversations on Android devices; very useful for instant messaging apps such as WhatsApp
A custom temporary folder can be chosen for extractions, making it easier to optimize your heavy-duty forensic laptops and touch devices for speed and size; quicker write speed if the location is on SSD
It is now possible to export in CLBX format
Samsung-specific messages can now be analyzed
App downgrade further improved
Analysis updates for many apps
Stability improvements
Multiple bug fixes and minor improvements
Interested in more details? Register for our free live hosted webinars here.